GSoC Week3
Date: June 27, 2022 → July 3, 2022
Tasks overview
- Add CI and tests for poem-casbin
- Take a look at casbin-grpc
- research
Task 1 Add CI and tests for poem-casbin
First I add CI for poem-casbin, ci.yml is bases on which from actix-casbin-auth, but I made some minor changes: change branch name from master to main , and upgrade actions/checkout to v3.
The workflow will run following checks when there’s push/pull_request to main branch:
cargo buildcargo test --no-default-features --features runtime-tokiocargo test --no-default-features --features runtime-async-stdcargo clippy -- -D warningscargo fmt --all -- --check
This is what we got:
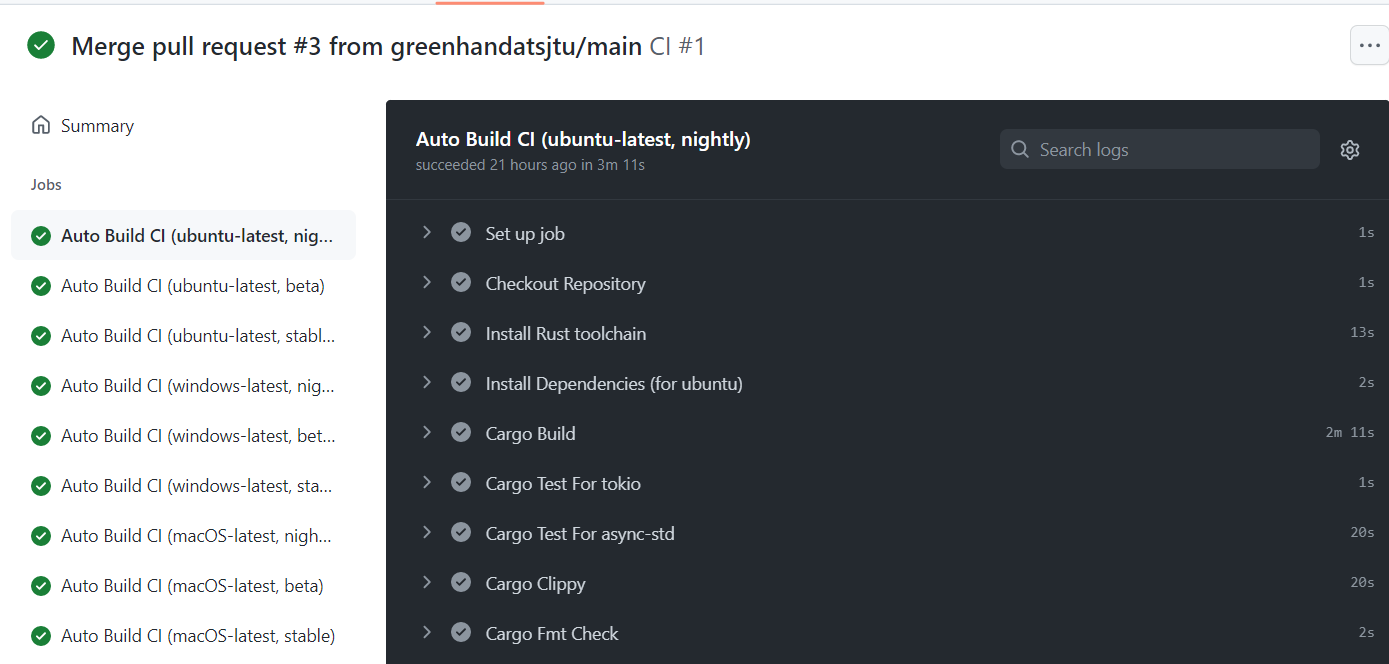
Then I started to add some tests and examples to poem-casbin, I also use actix-casbin-auth as reference, it has 3 test files:
- test_middleware.rs: test basic middleware function
- test_middleware_domain.rs: test middleware function with domain
- test_set_enforcer.rs: test initializing middleware using
set_enforcer()
In the tests, first it implements a fake authentication middleware called FakeAuth, which just simply insert a CasbinVals with subject alice and domain domain1 to request’s exetensions:
1 | fn call(&self, req: ServiceRequest) -> Self::Future { |
Then it wraps its endpoints in FakeAuth and casbin middleware:
1 | let mut app = test::init_service( |
As for poem, it’s a little different. To use test in poem, we have to enable test feature of it, then we can test like below:
1 | use poem::{handler, test::TestClient, Route}; |
And poem use with to wrap endpoints with middlewares:
1 | let app = Route::new() |
Note that casbin_middleware must be precedent than FakeAuth.
And I learned that to switch runtime I can use cfg_attr:
1 |
|
I made 2 PRs which got merged:
- https://github.com/casbin-rs/poem-casbin/pull/3 add github workflow that runs
cargo test/clippy/fmton push/pull_request - https://github.com/casbin-rs/poem-casbin/pull/4 add several tests/examples for poem_casbin_auth
Next week I’ll add README for this project.
Task 2 Take a look at grpc-casbin
For now, casbin-grpc build fails with bunch of errors:
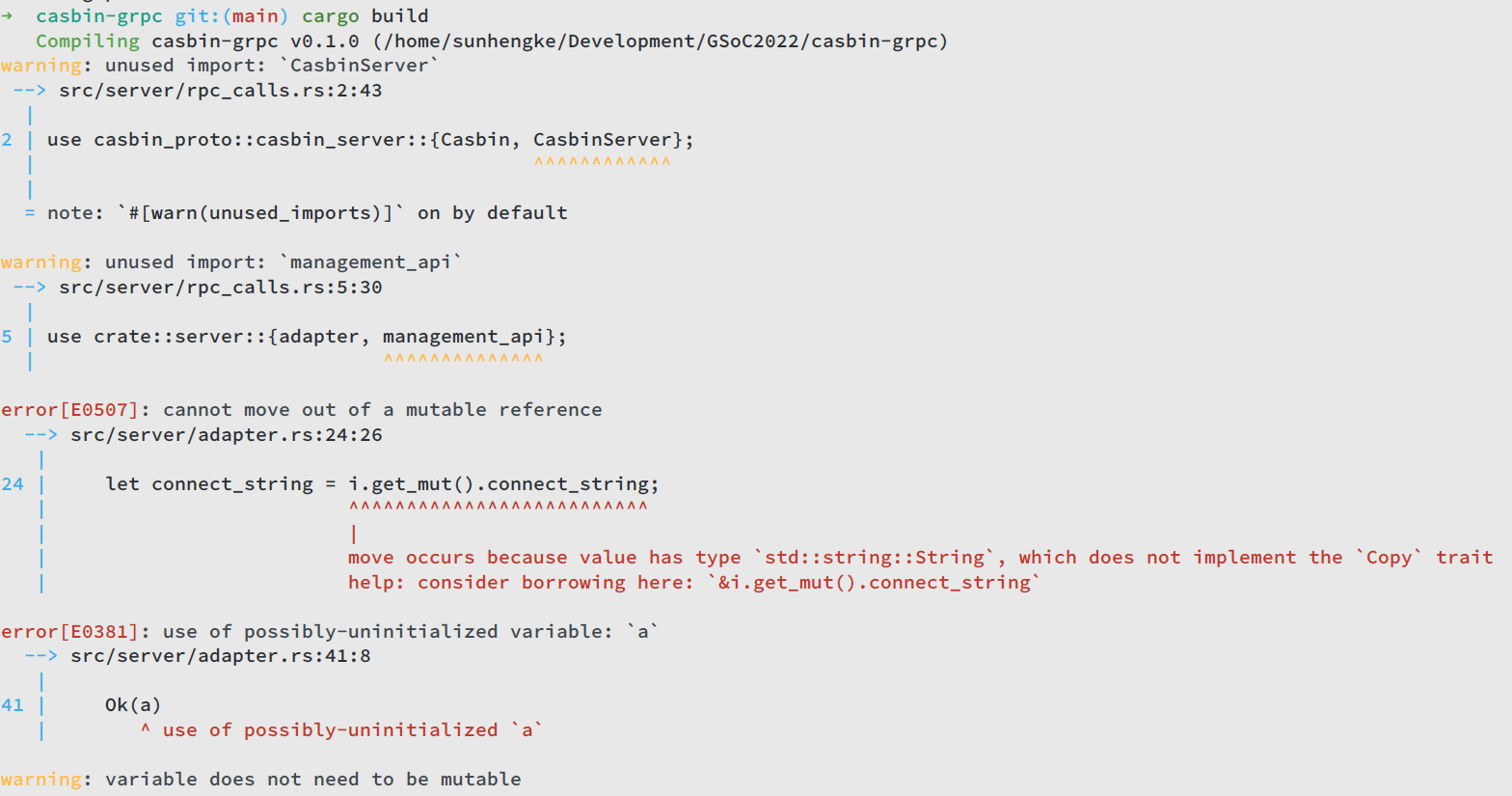
There are mainly 2 issues:
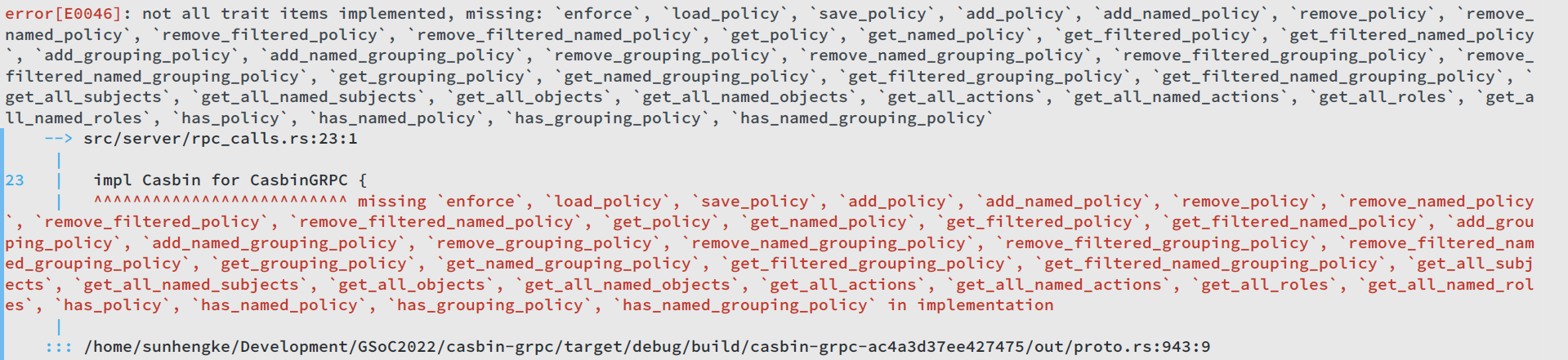
First, most functions of Cabin trait are not implemented:
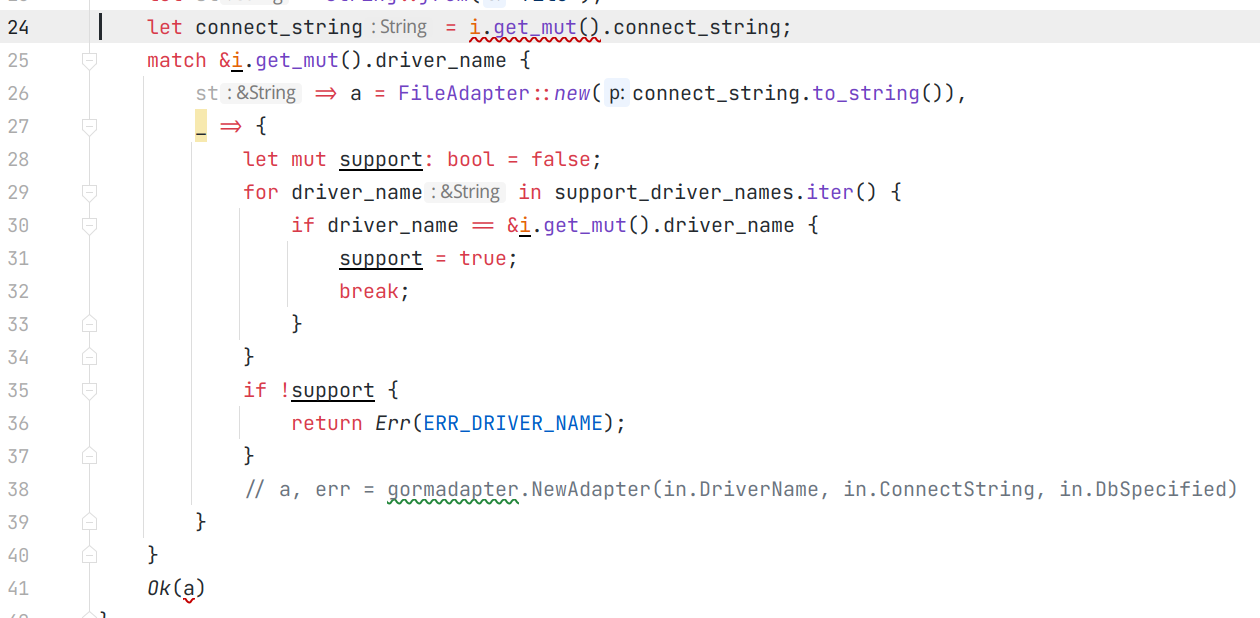
Second, new_adapter function only supports FileAdapter now:
I think I can work on this repo to complete it in the next few weeks.
Research on real-world application
After talked with my mentor last week, I know that casdoor-rust-sdk is assigned to another student, and I need to think of a new task.
I want to do something solid, and don’t want to use Rust just to write a web application. So after I researched a while, I think I can either:
combine casbin-rs and yew to implement a front-end access control framework like:
dufs is a distinctive utility file server that supports accessing control, we can maintain a fork of it and use casbin-rs as access control backend
complete grpc-casbin and colaborate with Siddhesh Kanawade on casbin-raft, as there are actually a lot of work to do